Practical Steps on How to Share Your Data Securely | WinGPG
In the digital era, data sharing is an essential aspect of our daily lives – it makes businesses work, helps people interact with each other and learn new things, and so much more. We’re so used to sharing data quickly via the Internet that the data security issue often recedes into the background.
Meanwhile, the security stats don’t seem encouraging. According to recent statistics, the number of data records exposed worldwide in Q3 2022 reached 14.78 mln of records which is 5 times higher than in Q2 2022 with 5.54 mln records (yet, not as bad as in Q4 2020 when the number of exposed data reached 125.74 records).
The number of cyber crimes related to data breaches grows early together with the amounts of data managed and shared online. And although world-known tech giants invest large sums of money into data security, data breaches happen once in a while. Sometimes, it’s much safer to store the data on a memory stick, that’s why hardware crypto wallets are considered the most secure, or use additional applications to ensure that the data is encrypted and transferred fully protected.
In this article, we’ll look at the data-sharing risks and find out how to share information securely.
Risks Involved With Data Sharing
Although individuals and companies are aware of how to withstand many situations with potential risks of data breaching, mistakes do happen. The main risks involved with data sharing can be summarized as the following:

- Sensitive data exposure – often, sensitive data is exposed accidentally by individuals or company employees as they don’t follow the data handling policies in the company or simply aren’t careful with the data. At the same time, cybercriminals can use elements of social engineering to fish some data out from an employee to get access to sensitive information through fraudulent means.
- Susceptibility to cyber attacks – this gets to the technical side of data sharing when people bypass firewalls while uploading/downloading files, use insecure protocols such as HTTP instead of HTTPS encryption and verification protocol, and more. This way, they become vulnerable to cyberattacks which can take many forms from DDoS attacks to a man-in-the-middle attack, and many others.
- Installing malware – this is a common way to lose secure data which involves the technical side and social engineering in combination. It’s when an employee is convinced to download a malicious application packed with various viruses, spyware, worms, and more.
Tools for Secure Data Sharing
Just a short time ago, the most natural way to share data was recording it on a CD disk or storing it on a memory stick. Today, all these means of data exchange have become irrelevant and people use cloud services instead to share their data quickly, smoothly, and conveniently.
To protect data from unauthorized access, cloud storages encrypt files before sending them. However, only several of them use end-to-end encryption. That’s because the services reserve to themselves the right to access the data they transit to avoid any legal issues such as sharing copyrighted materials or due to any inner service management reasons. This way, user data still remains visible to third parties. Therefore, when sharing data via cloud services, many companies also prefer using additional tools and means of extra protection.
Meanwhile, when it comes to cloud services, some of the most secure and popular are:
- Dropbox provides 2 GB of cloud storage for free, it’s simple to share files with this application and it automatically synchronizes data across all the devices linked to the cloud.
- GoogleDrive offers 15 GB of free cloud storage and provides additional services for document management like Google Docs, Sheets, and more. Companies can sign up for Google Suite which is a powerful workspace for online collaboration for businesses.
- OneDrive is a Microsoft alternative to GoogleDrive with 5 GB of cloud storage for free. With OneDrive it’s easy to link the Office pack to the cloud storage and keep the documents synced across all the linked devices.
- iCloud is the Apple storage that provides 5 GB for free. iCloud users can quickly share files with each other, edit them online, protect selected files with passwords, set an expiry date on shared links, and more.
Most Secured Ways to Share your Data
No data shared online can be protected 100% and businesses always take the risk of data leaking. File-sharing services attempt to address this issue effectively by implementing the latest technologies that help protect data. This can be the adoption of P2P (Peer to Peer) file transfer technology that works similarly to Blockchain. In P2P networks, data-sharing companies remove the central server for hosting data and use a distributed network with connected nodes instead.

Also, cloud services can use additional protection measures such as running in-cloud antivirus, implementing MFA (Multi-Factor Authentication), providing user access management, key management as a service, firewall as a service, and more.
There is a wide range of measures and services cloud providers offer to individuals and businesses to additionally protect their data. Meanwhile, companies and stand-alone users can also do much to improve their files’ security. Here are the best practices and steps to take:
- End-to-end encryption – opt for the services that use end-to-end encryption to protect your files from viewing by the host.
- Double-check permission settings – before sharing a link to your files stored on a cloud, make sure that you’ve set access permissions right and that no one else except for your partner can use the link to view the files.
- Continuous file audition – run file audits and check the access permissions for them. If the file is outdated, delete it from the system.
- Encryption software – use additional software to ensure that your files are secure to share via a cloud, a messenger, or e-mail services.
- Staff training – employee training on how to handle sensitive information is an integral part of effective data protection.
Find out more about how to protect your data in our 5 Ways to Secure Your Digital Content article.
How WinGPG Can Help to Keep Your Data Safe and Secure
One of the most effective ways to protect your data is to encrypt it. One of the best solutions for privacy protection is PGP and its Open Source implementation – GnuPG (GPG). However, there are no utilities that offer a user-friendly interface, easy navigation, and stable work at the same time. For this purpose, Scand developed its own free encryption tool – WinGPG.
WinGPG – an Open Source Encryption Tool based upon GnuPG. It is an easy-to-use Windows tool for file encryption, secure messaging and overall data protection. It is a classic Windows tray application and has an original GPGv2 distribution (no modifications are done to the official code). WinGPG is facilitating productivity far-forth by registering shortcuts and extensions into your system using GPG (via GPGme library) with proper options.
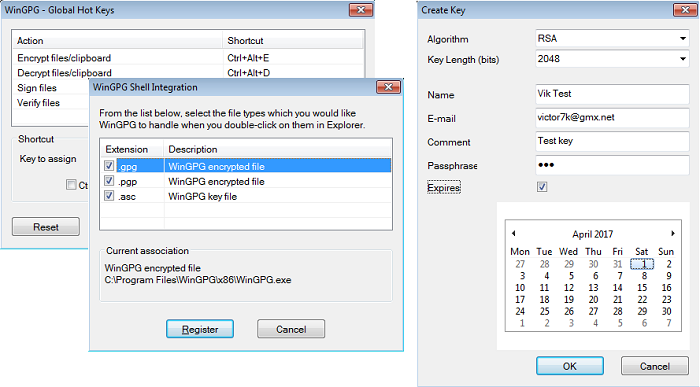
WinGPG application offers the following services:
- Simple key management from creation to revoking
- Strong encryption and easy decryption
- Easy signing and verification of files
- Smooth work with other applications such as Total Commander and FAR
- Clipboard support for texts and files
- Integrated hotkeys and context menus
What makes WinGPG different from its closest analogs?
First of all, you should realize that all allied software operates on the Kleopatra certificate management system. In case you have ever heard any feedback regarding Kleopatra you’ll feel the difference working with WinGPG. We managed to provide a stress-free encryption environment when you don’t have to read manuals on encryption operations or spend hours and hours of watching how other people are using it on Youtube.
We prioritized essential encryption functions combined in a pretty secure tool (openPGP windows) with a nice simple GUI.
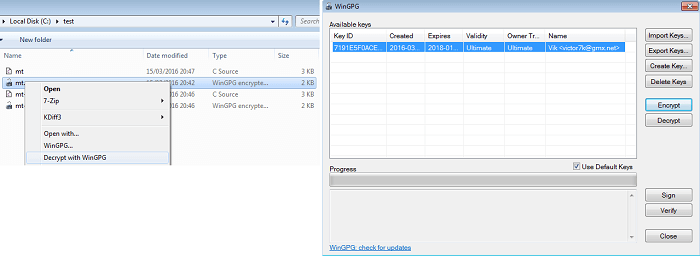
WinGPG can ensure secure delivery of files and messages, as well as provide verification of who created or sent the message using a process called digital signing at the click of a button. The software we created could also be used to secure sensitive files when they’re stored in vulnerable places like mobile devices or in the cloud. Even if you are using such apps as Whatsapp, Skype, Viber, etc. WinGPG could provide secure messaging.
We made our Windows encryption tool simple and as user-friendly as it could be. It doesn’t occupy much space, doesn’t seek for automatic updates and tries to reconnect to unknown cloud servers. It’s a humble tool and does only what it is supposed to: encrypt, decrypt, put a signature, verify a signature. The original GPG encryption code has not been modified, so if one day you decide to take gpg.exe and try to make it work with our GUI, you’ll be delighted how quickly they hit it off with each other.
WinGPG allows you to either create your binary keys by choosing from numerous algorithms and defining various other parameters, such as name, email address, comments, and passphrases. Additionally, you can set expiry dates for your keys, so that they can no longer be used after a certain period, thus ensuring your sensitive information a higher level of data protection.
However, the communication requires participation by both the sender and recipient and you will be surprised how intuitive its interface is. It has clipboard support, WinNT Explorer support, global accelerator and global shortcuts working from the active explorer window, clipboard and context menus.
Conclusion
Data security is a sensitive issue for businesses and individual users. Nevertheless, the number of data breaches is growing year by year together with the amount of data shared online. Therefore, companies and stand-alone users have to be better prepared for handling and preventing data leaks.
There are several steps users and businesses can take to minimize the risks of data leakage. This can be file access audition, use of reliable file hosting services, and utilization of additional level protection software. SCAND offers a simple and cost-free solution to ensure strong data security – WinGPG. Have any questions, ideas or simply want to give us feedback on WinGPG? Send us an email to wingpg@scand.com.












