Everything You Need to Know About Mobile App Vulnerabilities
Today, a smartphone with an internet connection is a primary tool for millions of people to stay in touch with their colleagues and relatives, make quick purchases, do business, exchange and store data, and much more. In 2020, there were over 4 billion unique mobile internet users around the globe, making over 90% of the world’s internet population. The number of smartphone users is steadily growing every year with 6,378 million users in 2021 and 7,516 expected by 2026. All these reasons make smartphones a tempting target for cybercriminals.
There are millions of users and companies that suffer from mobile app vulnerabilities every year.

All these stats signify that the security of mobile apps is a significant issue for businesses and their customers and it requires continued attention.
In this article, we’ll look into how mobile apps with a lack of security can negatively impact their users and businesses, what are the common security threat types, and how to secure your mobile app effectively.
Impact of Weak Mobile App Security
Mobile security is one of the major issues that concern everyone – from individual users to large corporations. There are a variety of ways how weak mobile app security can adversely affect businesses and individual users. Let’s have a closer look at them.
Disclosure of Private Data
By using a mobile app infected with a virus, hackers reach a mobile device’s functions. For example, they can obtain user’s logins from social media, emails, and banking, steal personal data on the device, change the smartphone’s settings like GPS location, IP address, send SMSes, and much more.
Infecting a smartphone with viruses is a popular way for cybercriminals to get the needed data. Statista has found out that the number of detected malware packages installed on mobile devices around the globe from 2015 to 1Q 2021 reached nearly 1.5 million cases.
Access to Financial Information
Once a user downloads a malicious package and installs it on their mobile device, all the data, including mobile banking logins, credit/debit card numbers, history of banking transactions, and other private data falls into the hands of hackers.
In 2020, Kaspersky laboratory reported on Ginp mobile Trojan virus. It tried to reach for the banking data of Spain, Poland, and the UK users by overlaying apps with phishing pages and generating fake SMS messages for their victims to get access to their banking data.
Intellectual Property Rights Violation
Mobile gadgets aren’t the only ones that suffer from hacker attacks, some cybercriminals aim at app code bases in order to create app clones. The more a mobile app becomes successful on an app store, the more attempts hackers will make to clone it. As a result, the original app loses its followers, revenue, and brand confidence.
Although there is no standard solution on how to avoid app cloning, app owners try to protect their apps in many ways by implementing app verification certificates, using app-protecting SDKs, and much more.
Key Types of Mobile App Security Threats
Once in 3-4 years The Open Web Application Security Project (OWASP), a non-profit foundation on software security, releases its Top 10 list of the most common security risks and vulnerabilities for mobile apps. Based on these common security threats, software engineers develop their app vulnerability tests and app protection procedures.
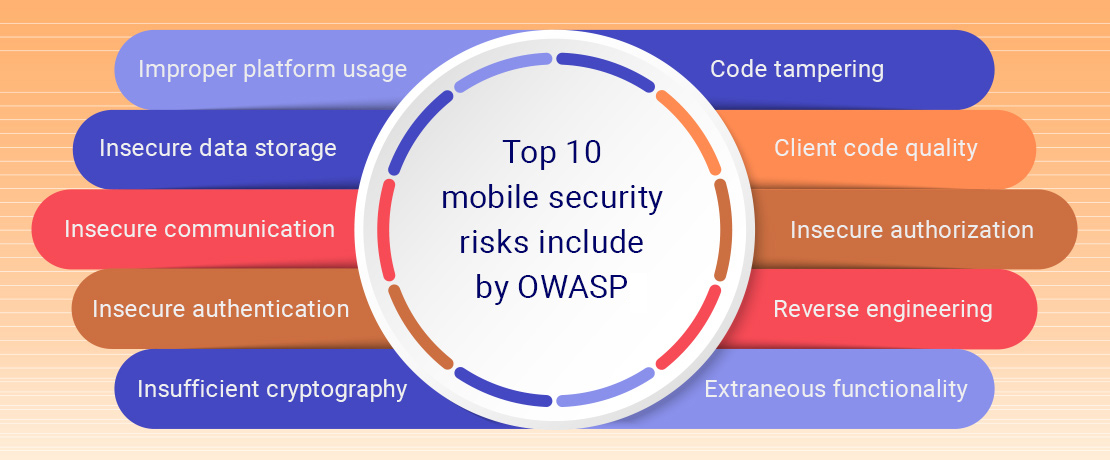
World-known IT security companies such as Kaspersky and CSO create their common security threats lists, relying on the OWASP rating. The latest Kaspersky and CSO mobile vulnerabilities update includes the following issues.
Data Leakage
Data leakage vulnerability can happen when sensitive data is sent from the server to the client as a response, in case of an app to app communication, application framework version disclosure, or through app caches.
The app can reveal sensitive data due to incorrect app or server configurations when the app has differences in page responses for valid and invalid data and other technical issues. Some other cases can include improperly locked and lost devices, downloading risky apps from unreliable sources, granting broad permissions to suspicious applications.
Unsecured Wi-Fi
Public unsecured Wi-Fi connections provide free internet access but neglect the necessity to encrypt the transferred data. Public unsecured networks don’t have any strong password validation. This significantly increases the risks of data being intercepted by hackers, including login credentials in banking accounts and social media networks, identity theft, and others.
IP Spoofing
With IP spoofing hackers can perform malicious actions without being recognized. For this, they use the IP address of another device to disguise themselves as a trusted source to gain access to their victim’s device. Cybercriminals use IP spoofing to steal personal data or flood and put down websites and corporate servers.
Spyware
Spyware is a type of malicious software that gathers data and monitors the activity of a client and secretly sends sensitive data to their creators. This type of software monitors emails, SMS, and MMS messages, intercepts of live calls, and much more.
Often, users don’t even know that there is spyware on their mobile phones. For spyware to appear on a smartphone it should be downloaded and installed by someone. Therefore, users should be aware of who uses their mobile gadgets.
Broken Cryptography
To ensure strong protection of data transmission, mobile developers should use data encryption protocols like TLS, especially when it comes to authenticated connections.
Another problem of insufficient data encryption can happen inside a mobile app logic. Some software engineers can compromise security to speed up the development process, leaving back doors in the code for cybercriminals. As a result, hackers don’t even need to crack mobile app passwords to get into the system and do harm.
Improper Session Handling
Mobile apps use session tokens to facilitate mobile device transactions between a user and a server. These tokens help apps to identify users and validate them. They are added to each service transaction and perform smooth authentication and authorization for any service request.
Improper session handling occurs when app tokens are unintentionally shared with third parties when performing app/server transactions. Cybercriminals can use this data and hack the app system. Therefore, mobile developers should always ensure that new token generations and app sessions remain confidential.
Phishing Attacks
Mobile devices are especially vulnerable to phishing attacks whose popularity grew over 600% during the Covid-19 pandemic. This happens as users started using their mobile devices much more often when working from home, e.g. for monitoring their emails or messengers in real-time.
When performing phishing attacks, hackers pretend to send emails from reputable businesses like Amazon or Google, asking to verify their credentials by following a link in an email. Apart from emails, cybercriminals can use SMS phishing, social media channels, popular messages, and others.
Best Practices of Securing Your App
Mobile application security is one of the major issues that mobile developers strive to handle at their best when they create their products. However, to ensure that the built app is risk-free and it doesn’t reveal any personal data to third parties, developers, product owners, and end-users should take care of mobile security.
What developers can do to ensure strong mobile app safety:
- follow The Mobile Security Testing Guide (MSGT) by OWASP;
- choose secure and effective mobile development tools;
- apply minimal application permissions;
- develop proper mechanisms for guarding sensitive data;
- use encryption certificates and protocols;
- perform app penetration testing;
- minimize the use of third-party libraries;
- restrict user privileges.
What product owners can do to improve the mobile security of their apps:
- together with the development team perform a risk analysis of the developed app, e.g. conduct threat-modeling exercises when all the stakeholders discuss the app features and ways of how the app can be attacked or compromised;
- choose the right development architecture and consider all the security risks;
- consult security experts;
- perform occasional app testing for vulnerabilities;
- choose a reliable mobile development partner.

What end-users can do to secure their data:
- avoid saving passwords on their mobile devices;
- log out from their apps, especially banking and payment apps, before moving to other apps;
- use multi-factor authentication;
- avoid unsecured public Wi-Fi;
- use reliable antivirus on their mobile gadgets.
Summary
In mobile development, mobile application security is one of the major issues that software developers are constantly working on. Every year there appear new hacking methods and techniques that IT companies have to respond to.
At the same time, not only software developers can work on the improvement of mobile app data. Project stakeholders and end-users can also do much to protect their mobile apps and the data they hold.












