Mobile App Security: How to Safeguard Data
Today, a smartphone with an internet connection is a primary tool for millions of people to stay in touch with their colleagues and relatives, make quick purchases, do business, exchange and store data, and much more. In 2020, there were over 4 billion unique mobile internet users around the globe, making over 90% of the world’s internet population. The number of smartphone users is steadily growing every year with 6,378 million users in 2021 and 7,516 expected by 2026. All these reasons make smartphones a tempting target for cybercriminals.
There are millions of users and companies that suffer from mobile app vulnerabilities every year.
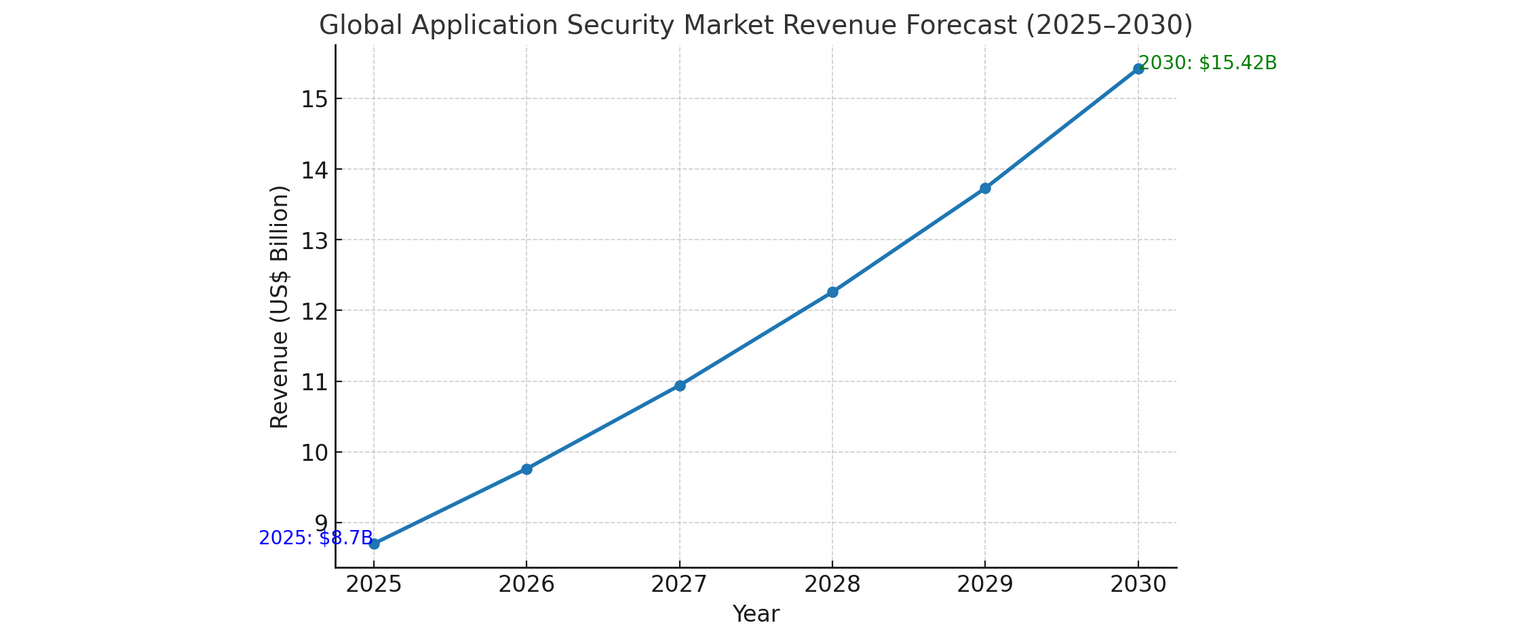
Global Application Security Market Revenue Forecast (2025-2030)
What Is Mobile Application Security?
Mobile application security is the set of practices, standards, and measures implemented during mobile application development to protect apps from cyber attacks, unauthorized access, and data breaches.
It entails everything from encryption and secure coding practices to industry regulatory compliance and authentication protocols.
Some measures are universal and apply to all types of applications, while others target specific mobile aspects, such as sensors, device permissions, secure storage (keychain/keystore), GPS, biometric login, and persistent network connections.
Why Mobile App Security Matters
Unlike traditional desktop software, mobile apps run on devices that are always connected to the internet and often filled with sensitive financial and personal data.
Therefore, the purpose of mobile app security must go far beyond maintaining technical integrity. For users, it means creating confidence so that they know their private data stay safe.
For companies, it’s the foundation of credibility and a safeguard against irreparable financial and reputational damage: once users lose trust in an app, they are unlikely to come back, and word spreads fast.
Types of Mobile Security Threats
Threats in mobile app security mainly target the application’s code, data handling, or the way it interacts with users. Unlike general device-level risks, these dangers focus specifically on exploiting weaknesses in how an app is designed, developed, or used.
Mobile app security risks are usually divided into two groups: passive threats and active threats.
Passive threats are vulnerabilities within the app itself. These could include weak or missing data encryption, outdated security libraries, insecure APIs, or flaws in the authentication process. While they may not cause immediate harm on their own, they leave “backdoors” that attackers can exploit later.
Active threats, in turn, are overt hacker intrusions. They are further subdivided into:
- MITM (Man-in-the-Middle) attacks – interception of network traffic between the app and its server.
- Reverse engineering and code tampering – analyzing or modifying app code to bypass security checks or insert malicious functionality.
- Rooting and jailbreaking exploits – gaining full control over a device, which allows attackers to interfere with app security mechanisms.
- Trojan apps and malicious deep links – harmful apps or links disguised as legitimate ones to steal data or trigger unwanted actions.
- Malware and spyware – malicious software that covertly accesses sensors, SMS, storage, or tracks user behavior.
Together, whether passive or active threats, they can lead to stolen identities, lost money, or sensitive data sold online. Knowing the typical dangers is the start of protecting mobile apps and their users.
Key Benefits of Mobile Application Security
The application security market is driven by high investments, resulting in a market volume of $8.70 billion, according to Statista. But for many companies investing in security, it is important to understand how much they could get in return and whether those benefits are worth investing in.
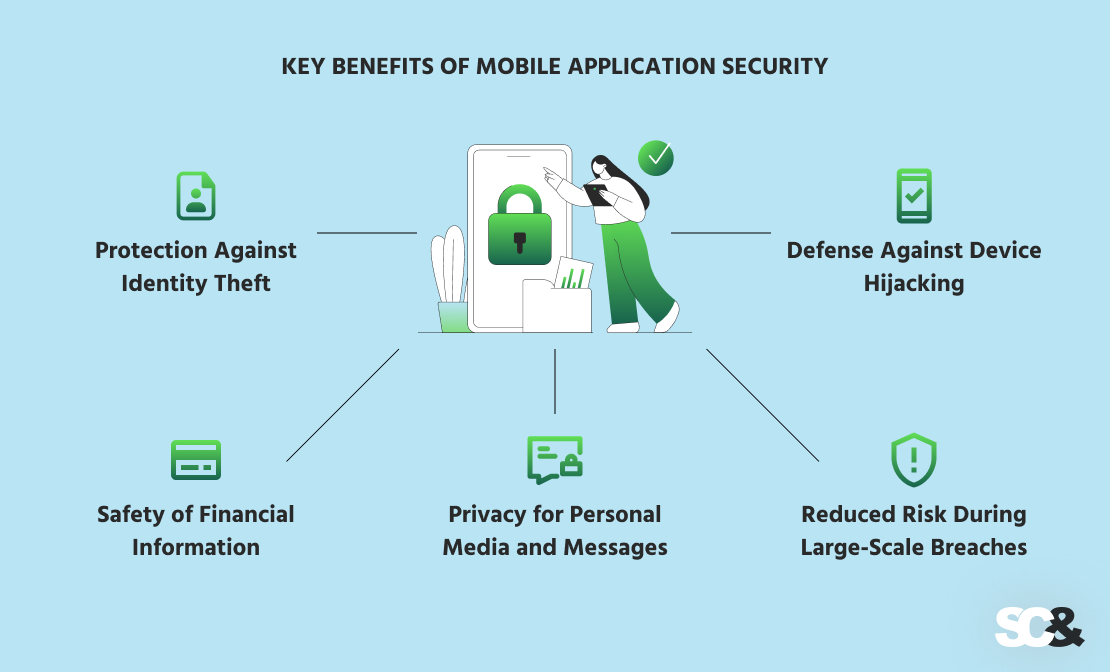
Protection Against Identity Theft
Secure apps prevent attackers from accessing sensitive personal information, such as IDs, passwords, or authentication codes. Without protection, users risk identity theft, which can lead to fraudulent accounts or unauthorized transactions.
For businesses, a breach of user identities can result in lawsuits, regulatory fines, and long-term reputational damage.
Safety of Financial Information
Many mobile apps handle sensitive payment data, including credit card numbers, bank account details, and transaction histories. If security fails, users may face financial losses, while businesses risk chargebacks, fines under PCI DSS compliance, and loss of customer trust.
Privacy for Personal Media and Messages
Mobile devices often store layers of private content. In case of a breach, users may experience blackmail, harassment, or embarrassment, while businesses could face lawsuits or negative media coverage.
Reduced Risk During Large-Scale Breaches
Even major corporations are vulnerable to massive data leakages, which can expose millions of users’ personal data. For companies, sufficient security reduces legal exposure, limits financial penalties, and preserves consumer confidence.
Best Practices to Enhance Security in Mobile App Development
Since attackers always look for new ways to break into apps, developers need to stay one step ahead and use proven methods to secure mobile applications.
A strong foundation for this work is the OWASP Mobile Security Project, which provides the MASVS (Mobile App Security Verification Standard) and the MASTG (Testing Guide). These resources describe what secure apps should look like, how to test them, and how to get rid of weaknesses.
Detection of Security Flaws
The first step is always to reveal possible entry points before attackers find them:
- Static Testing (SAST). Scanning source code early (for example, by using SonarQube or Fortify) helps catch unsafe patterns like hardcoded credentials or cryptographically poor functions before they reach production.
- Dynamic Testing (DAST). Testing a running application shows problems that static scans might miss. Here, it’s possible to apply OWASP ZAP or Burp Suite to safely simulate attacks.
- Penetration Testing. To get a better side view, security experts can act like attackers, trying to bypass login, intercept API traffic, or extract sensitive data from local storage. They can either rely on frameworks like Metasploit or use manual testing methods to uncover hidden weaknesses.
- Threat Modeling. Mapping out potential abuse scenarios prevents overlooked attack paths, such as tampered APIs or session token misuse. For example: What if someone tampers with the checkout API in an e-commerce app? What if session tokens are reused in a trading app? For these purposes, teams can use Microsoft Threat Modeling Tool or OWASP Threat Dragon to visualize risks and plan mitigations.
- Automated Pipeline Scanning. Integrating security checks into CI/CD guarantees vulnerabilities are caught before each release. To automate these scans, developers can use platforms such as GitHub Advanced Security or Veracode.
Fixing Vulnerabilities and Strengthening Protection
After finding problems, developers need to fix them quickly and add safeguards:
- Regular Updates. Many breaches, like the Equifax case, happened because of missed patches. Keeping software and libraries up-to-date closes known security gaps that attackers exploit most of all.
- Strong Encryption. Encrypting data in storage and transit protects sensitive information from breaches. For these purposes, developers can combine AES-256 for stored data, TLS 1.3 for data in transit, and Key Management Systems (KMS) for key handling.
- Regulatory Compliance. Adhering to PCI DSS, HIPAA, and other standards proves apps handle data securely and legally. In order to simplify verification and reporting, developers can use compliance frameworks or auditing tools such as Vanta or Drata.
- API Security. Attacking APIs is not a rare case. To cope with this problem, developers apply OAuth 2.0, API gateways like Kong or Apigee, and rate-limiting techniques that help prevent unauthorized access or data manipulation.
- Runtime Protection. Apps should detect unsafe environments. For instance, a banking app running on a rooted or jailbroken device should block transactions. For these purposes, it’s possible to apply tools like AppShield or RASP solutions from Contrast Security.
- Zero Trust Approach. Verifying every request (even from logged-in users) minimizes insider and lateral attack risks. To enforce this approach, it’s a good idea to apply multi-factor authentication (MFA) and identity management (IAM) systems.
Regular Security Practices
Security never ends at launch. Regular monitoring and overseeing can greatly contribute to further safety reinforcement:
- Code Reviews. Peer reviews uncover logic flaws and subtle security issues that automated tools might miss.
- DevSecOps. Embedding security into the CI/CD pipeline guarantees every release is checked before going live.
- Monitoring & Alerts. Apps should log suspicious activity, such as repeated failed logins or unusual geographic access, and alert the team immediately.
- Bug Bounty Programs. Many companies, including Google and PayPal, often invite ethical hackers to spot vulnerabilities that internal teams may overlook.
Overall, early detection of vulnerabilities and their elimination using existing procedures allows to significantly reduce possible threats. The result is a mobile application that fully complies with international standards and gets long-term trust of users due to its resistance to any attacks.
| Threat | How to Detect | How to Protect |
| Insecure data storage | Code review, penetration tests | Encrypt data (AES-256), avoid local caching |
| Outdated libraries | Dependency scanning | Regular patching, CI/CD updates |
| Weak authentication | Brute force simulation | Strong passwords, MFA, account lockouts |
| Insecure communication | Network traffic analysis | TLS 1.3, SSL pinning |
| API exploits | API testing, fuzzing | OAuth 2.0, rate limiting, server-side checks |
| Malicious libraries | Static analysis | Use trusted sources, verify signatures |
Why You Should Choose SCAND for Mobile App Security
After a massive hacking event in August 2023 that disclosed the private information of around 760,000 users, Discord.io went offline. The shutdown was claimed to be a decision to avoid lawsuits resulting from the breach.
A different incident happened to the Tea Dating Advice app. During July 2025, it leaked numerous personal user photos and private messages, which led to multiple class-action lawsuits and raised concerns about the app’s privacy.
Following these examples, it becomes clear that decent mobile app security is non-negotiable. But how to incorporate security tools so that applications can get the most out of them?
At SCAND, we combine over 25 years of software development experience and time-tested security practices to deliver mobile solutions with the utmost protection.
Our team consists of seasoned Android and iPhone developers who ensure compliance with high-level frameworks and regulations, including OWASP, ISO, GDPR, HIPAA, and more.
If you’re looking to create mobile apps that users can trust, our experts are ready to help. Contact us to hire mobile app developers and create a secure and future-proof solution adapted to your needs.












