You’re giving your contractor access to your data, ideas, and customer databases — but how well are they actually protected?
In today’s digital world, high-quality development alone is no longer enough. Clients are increasingly concerned about where their data is stored and who can access it.
That’s why more and more IT companies are implementing ISO 27001 — an international information security standard that’s not just a fancy certificate on a presentation slide, but a real shift in how projects and client relationships are handled.
In this article, we’ll explain why ISO 27001 isn’t about paperwork. You’ll learn how it helps businesses feel confident about their data, builds client trust from the very first stage of cooperation, and directly impacts the result — from the initial requirement discussion to the secure maintenance of the final software product.
What Is ISO 27001?
ISO 27001 is an international standard that helps companies protect their data. It answers the key question: what you should do to make sure information doesn’t leak, get lost, or end up in the wrong hands.
But most importantly — this standard isn’t just theory. It’s highly practical, especially in the field of custom software development. When building a product from scratch for specific business needs, it’s crucial that it not only works but also keeps all internal information secure — from customer data to business logic.
It covers risk assessment, access protection, process control, and continuous improvement. Thanks to this, security isn’t treated as a one-time task — it becomes a natural part of the development culture and is integrated into the project itself.
In short, ISO 27001 is about building software people can trust — today and in the long run. To illustrate the growing popularity of ISO 27001 in the field of information security, we suggest considering a graph based on data from the annual ISO Survey report.
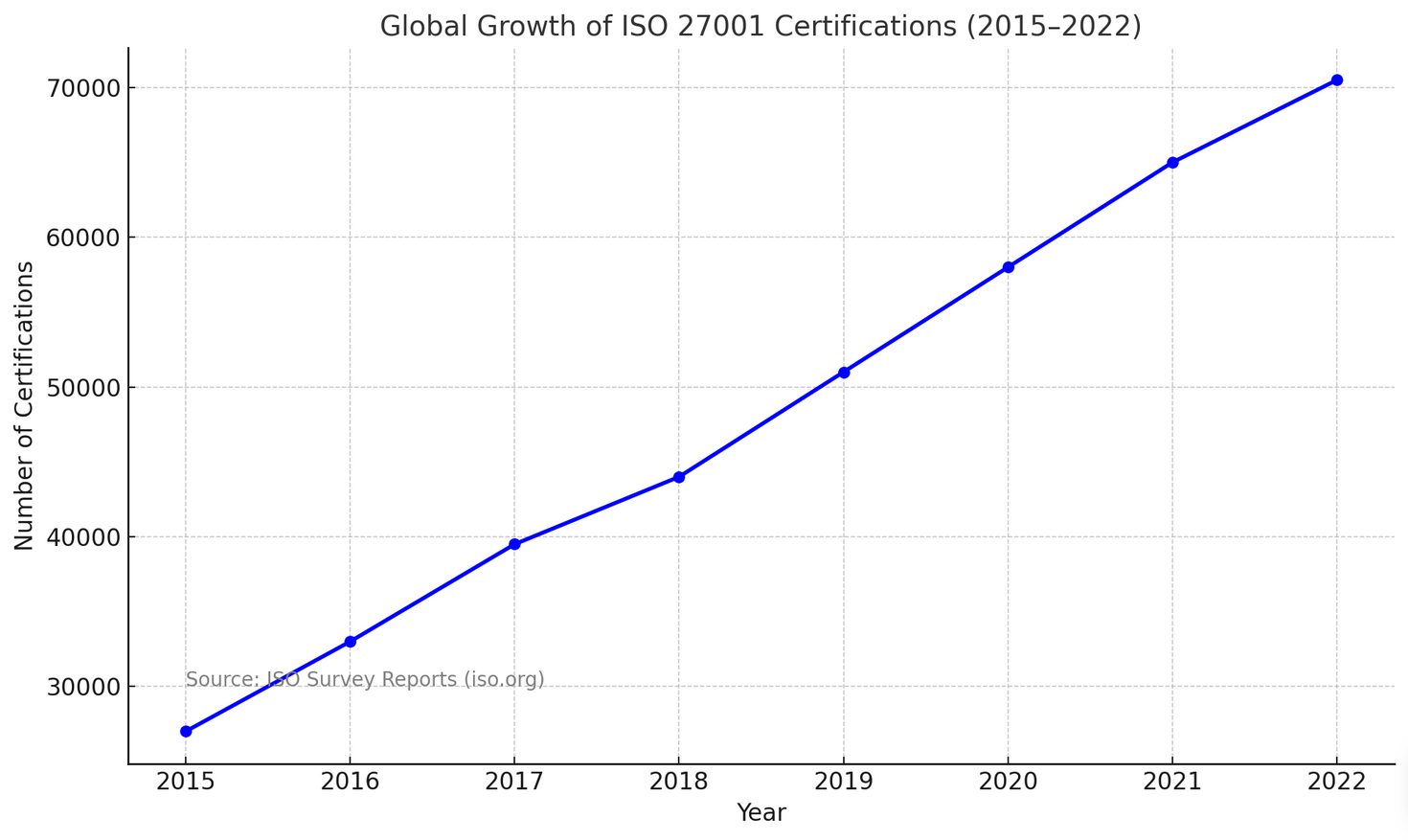
Global Growth of ISO 27001 Certifications (2015–2022)
How the Certification Process Works
ISO 27001 certification takes place in several stages. First, the company prepares an information security management system (ISMS): describes processes, conducts risk assessments, and develops policies.
Then an internal audit is conducted to identify and eliminate weaknesses (it checks whether internal policies and procedures are in place and functioning as expected).
After preparation and internal audit, the company undergoes an external audit — a full audit from an independent certification center (it verifies compliance with ISO 27001 requirements, assesses the effectiveness of the ISMS, and checks how well the system is implemented in real operations).
If everything is in order, the organization receives a certificate for 3 years. During this time, surveillance audits are conducted annually to confirm compliance with the standard, and recertification at the end of the period.
This process allows companies to not only gain compliance status but also build a sustainable data protection system with continuous improvement.
Impact of ISO 27001 on Custom Software Development Services
Implementing ISO 27001 in software development has a significant impact on data security, risk management, and process quality. Below, we look at how this standard helps protect information, prevent threats, and improve the reliability of development. These benefits make ISO 27001 an important tool for modern IT companies.

Security Improvement
Implementing ISO significantly enhances the level of information security in custom software development projects.
Every data-related process — from requirements gathering to storing user information — is governed by clearly defined rules and procedures. This ensures secure handling of sensitive customer data, including personal information, financial details, and business logic.
Risk Management
One of the core goals of an ISO certificate is proactively identifying and managing risks before they become real problems.
In a developing environment, it means everything from running vulnerability tools to being prepared for the unexpected. This practice helps avoid data breaches, service outages, and several other major incidents.
Quality Assurance
ISO 27001 has an impact beyond security — it helps make development processes better overall.
Having well-documented processes, restricted access, regular audits, and employee training help make the process stable, predictable, and in accordance with the industry standards.
As a result, clients receive not only a functional product, but also the confidence that it has been developed in a structured, secure, and professionally managed environment.
Boosting Customer Satisfaction and Trust
ISO 27001 is a persuasive argument in favor of a development partner that has a systematic strategy for security and understands how to maintain data security throughout the various phases of the project.

For clients — particularly in sectors such as finance, health care, and e-commerce — it’s essential. They work with sensitive information, personal data, and financial transactions, and they want to ensure that everything is processed securely.
ISO aids reduce risk and boost the trust between client and vendor. It leads to fewer questions and less bureaucracy when onboarding and greater trust in a lasting partnership.
For example, in practice, enterprises with ISO certification have a distinct competitive edge when bidding for tenders and long-term contracts — even when a minimum viable service fulfills the business objective. It’s not merely a “checkbox” — it’s a tangible asset for forging strong relationships and reputation.
Achieving Continuous Improvement and Compliance
ISO 27001 is a living, constantly evolving mechanism that helps businesses build a truly mature approach to security policies. The standard teaches companies to regularly ask themselves important questions: where the weaknesses are, what threats are relevant today, and how to protect what really matters to the company and customers.
It is not only about the technical side but also about how the team thinks, works, shares information, stores documents, and responds to unusual situations.
When you’re dealing with customer’s personal data, medical records, or financial transactions, it’s not enough to just “promise security”. You need a transparent, understandable system that you can trust.
ISO certification is just such an indicator of maturity: it confirms that a company not only understands the importance of security but also knows how to work with it — in accordance with international rules, GDPR, HIPAA, and other regulations.
In practice, this means that a company has a clear structure: who has access to the data, where and how it is stored, and how quickly it can be reacted to if something goes wrong.
This structure helps avoid chaos even in times of growth or scaling. When a client comes to such a company, they feel confident that their ideas, their project, and their data are safe. And it is this confidence that turns ordinary development into a full-fledged partnership.
Case Studies and Success Stories
Real-life case studies of companies that have implemented ISO 27001 show how the quality standard helps strengthen security, increase customer confidence, and expand into new markets.

SCAND
SCAND, an international software development company, has achieved ISO/IEC 27001:2013 certification from the International Organization for Standardization, enabling it to:
- Demonstrate a commitment to data protection and regulatory compliance
- Strengthen competitive advantages in the market
- Optimize internal processes and reduce costs associated with security incidents
The ISO/IEC 27001:2013 certification verifies that SCAND has implemented and maintains an Information Security Management System (ISMS) that fulfills the requirements of the standard.
This certification applies to all structural divisions of the organization and is obligatory for all employees. Regular audits by authorized bodies help maintain compliance and safeguard sensitive information.
Additionally, SCAND is certified according to the ISO 9001:2015 quality management standard, further demonstrating its commitment to delivering high-quality and secure applications and products.
Altkom Software
Altkom Software implemented ISO 27001 to create a centralized information security system. This allowed them to:
- Reduce vulnerability to cyberattacks and external threats
- Increase customer confidence through transparent processes and adherence to international quality
ENTERBRAIN Software GmbH
ENTERBRAIN, a software company specializing in software development for non-profit organizations, implemented ISO 27001 to protect confidential information. The results include:
- Effective protection of information, data, and business processes
- Increased transparency in business processes and protection objects
- Competitive advantage thanks to ISO 27001 certification.
Quix
Quix, a streaming data platform, faced resource constraints when attempting ISO 27001 certification. Collaboration with Cognisys enabled Quit to:
- Successfully complete certification despite limited resources
- Build trust with clients, including companies such as McLaren and Deloitte
- Improve internal security and compliance processes.
Doccle
Doccle, an online administrative document management platform, enforced ISO 27001 and ISO 9001 to improve security and quality. This has resulted in:
- Building user trust through transparency and reliability
- Compliance with the requirements of GDPR and other regulatory standards
- Improving internal processes and operational efficiency
Relevant Software
Relevant Software, an international software development company, has achieved ISO 27001 certification to:
- Demonstrate a commitment to data security and regulatory compliance
- Strengthen competitive advantages in the market
- Optimize internal processes and reduce costs associated with security incidents
Challenges and Considerations in ISO 27001 Implementation
Although obtaining ISO 27001 certification brings clear advantages to a company, the implementation process can be challenging — especially for software development teams.

Developers are often great at technology but may lack experience in information security. On top of that, the standard requires changes to common workflows and the introduction of new rules, which can cause resistance among team members.
For companies with a flexible, startup-like culture, switching to a more formalized approach can be especially difficult — it involves documenting actions, assigning responsibilities, and running regular audits.
Including an outside consultant who helps avoid errors and save time can simplify the procedure.
Involving the team from the start is also absolutely vital — through active engagement, clear goal communication, and training. This means the change to the new system will feel more like a sensible move forward than additional bureaucracy.
Time, resources, and cost needed to obtain ISO 27001 certification:
- Timeline: 3 to 12 months — depending on company size and process maturity
- Costs: from $10,000 to $50,000+ (including consulting, implementation, and certification)
- Resources: Involvement of IT, HR, legal, and management will be required, especially at the stage of documentation and internal audits
Conclusion
ISO 27001 certification is a serious step for any custom software development company. At a time when security has become an integral part of IT products, this standard allows you to build a reliable system of information protection and strengthen the quality of all processes.
First of all, the international level for information security helps perform a structured information security management system (ISMS) — it is not just formal instructions but a comprehensive approach to reducing exposure to digital threats and control over how sensitive data is processed, transmitted, and stored.
For companies that develop custom software solutions, this international standard provides guidance on how security measures really work, how to organize a team, how to respond to incidents, and how to meet the requirements of highly regulated customers in the financial, medical, and government sectors.
Moreover, the implementation of the standard strengthens the quality management system within the company. This allows not just to execute projects but to do it predictably, consistently, and according to the best practices.
ISO 27001 helps build internal discipline and a culture of information security – where each team member understands what they are responsible for and how their actions affect the entire project.












